A computer network is a telecommunication network that allows the exchange of data between two or more computers. Computer network plays an important role in our day to day life. So it is necessary to secure our computer network from external attacks and malware. The use of cryptography techniques is one of the secure ways to protect our computer network. In this article, we are going to discuss cryptography and algorithms used for encryption. Cryptography helps to enhance the security of your computer. Lets us start with discussing some terms.
 What is Encryption?
What is Encryption?
In cryptography, encryption is the process of transferring messages to the secret message so that only authorized personnel who have the key can read it. One key is used to encrypt the data with secret data and another key is used to decrypt the secret data so that an authorized user can read it.
What is Cryptography?
Cryptography is an art & science of writing the secret message. It is used to secure private communication or data from being stolen. Cryptography not only protects the data from theft or alteration but can also be used for user authentication. Cryptography helps to maintain the integrity of the data. In Cryptography the plain text (Normal message) is encrypted or converted into Ciphertext (Secret message) which can only read by the authorized individual who has the key. Basically, there are three types of algorithms to do it.
1. Symmetric Cryptography or Secret Key Cryptography:
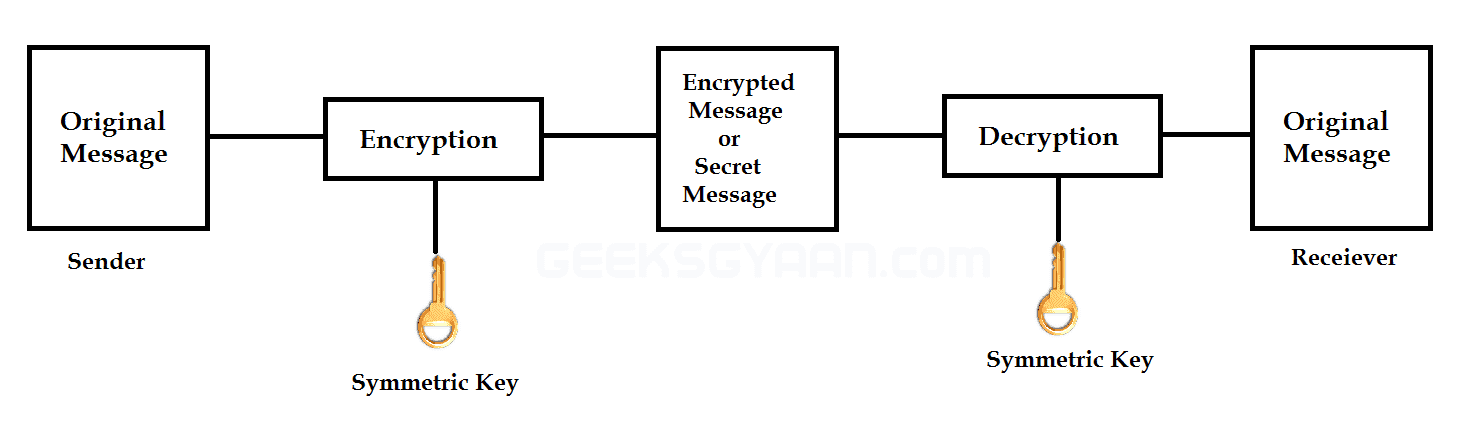 |
| Secret Key Cryptography or Symmetric Cryptography |
It uses a single key for both encryption and decryption. The key must be kept secret by the sender and receiver (no one else) because they need the same key to encrypt and decrypt the message. Therefore, it is known as secret-key cryptography. There are some algorithms used for symmetric cryptography for encryption & decryption. The following are the most popular algorithms used by symmetric cryptography.
- Data Encryption Standard (DES): It is the most widely used technique. DES was developed in 1970 as a US-government standard for protecting non-classified information and was published as a Federal Information Processing Standard. DES encrypts 64-bit plain text blocks under the control of 56-bit keys. Each key is extended by a parity bit to give a 64-bit working key.
- Advanced Encryption Standard (AES): It is an encryption standard developed by the US National Institute of Standards and Technology (NIST) in 2001. AES has a fixed size of 128-bit block data and a key size of 128, 192 or 256-bits.
2. Asymmetric Cryptography or Public Key Cryptography:
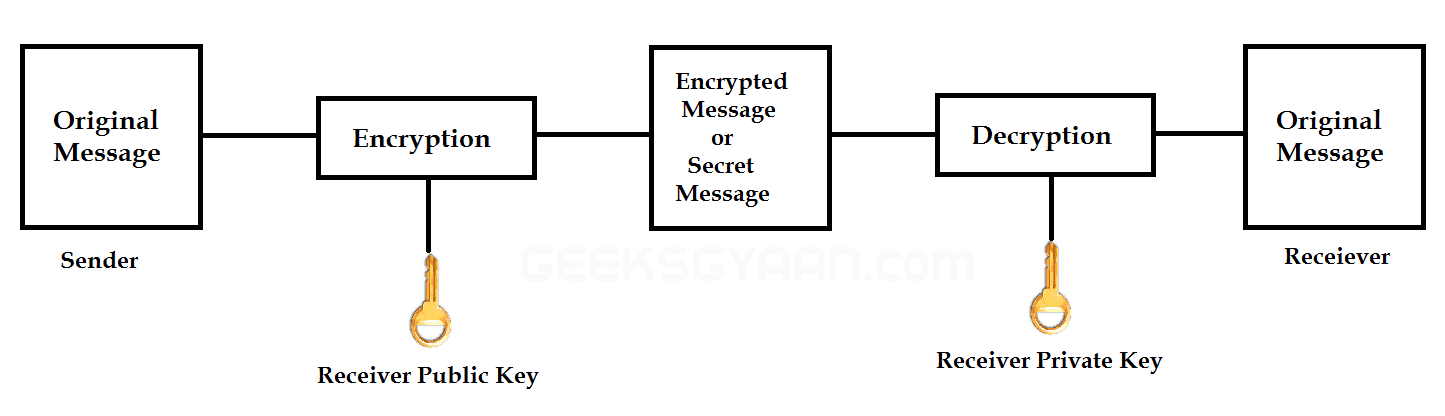 |
| Public Key Cryptography or Asymmetric Cryptography |
An asymmetric cryptography or public-key cryptography is a form of encryption where keys come in pairs. What one key encrypts, only the other can decrypt. Frequently keys are interchangeable, in the sense that if the key ‘A’ encrypts the message, then key ‘B’ can decrypt it, and if key ‘B’ encrypts a message, then key ‘A’ can decrypt it. Therefore, it is also known as Public Key Cryptography, because the sender and receiver have a separate key to read the message.
Where Can Cryptography Be Used?
Cryptography is used by organizations to protect top-secret, confidential data from outsiders or theft. Such organizations are- Military & Government organizations, Banks use it to protect their clients’ details, Many industrial organizations use it for keeping digital information secret. Electronic commerce websites use cryptography to secure credit card and other information about their clients, Email also uses cryptography to secure the message.





